Various news stories have been published lately where national level leaders are discussing cyber weapons and capabilities that are being developed. When airpower was being developed many early theorists believed that aircraft could and would be used to decisively win future wars without the aid of any other traditional forms of warfare. The mrxcls version uses a stub with a total size of bytes. Until recently it was unclear what the purpose of this file was, but popular opinion held that it was related to Stuxnet. There is no clear-cut answer here. However, no matter how powerful airpower became it was still only one tool of political and military power for nation-states. As nation-states discuss these types of cyber weapons more openly there will be a push for cyber deterrence that will result in more capabilities being displayed for the world to see. 
| Uploader: | Daidal |
| Date Added: | 26 October 2004 |
| File Size: | 20.70 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 50868 |
| Price: | Free* [*Free Regsitration Required] |
Ten Takeaways from the Tilded Platform
Jerry Shaw on This tells a team developing cyber weapons not only what they can do to hide their malware better but what to insert or remove from the malware to cause platorm ideas to be generated. The first modification of the Stuxnet worm, created inused only one driver file — mrxcls.
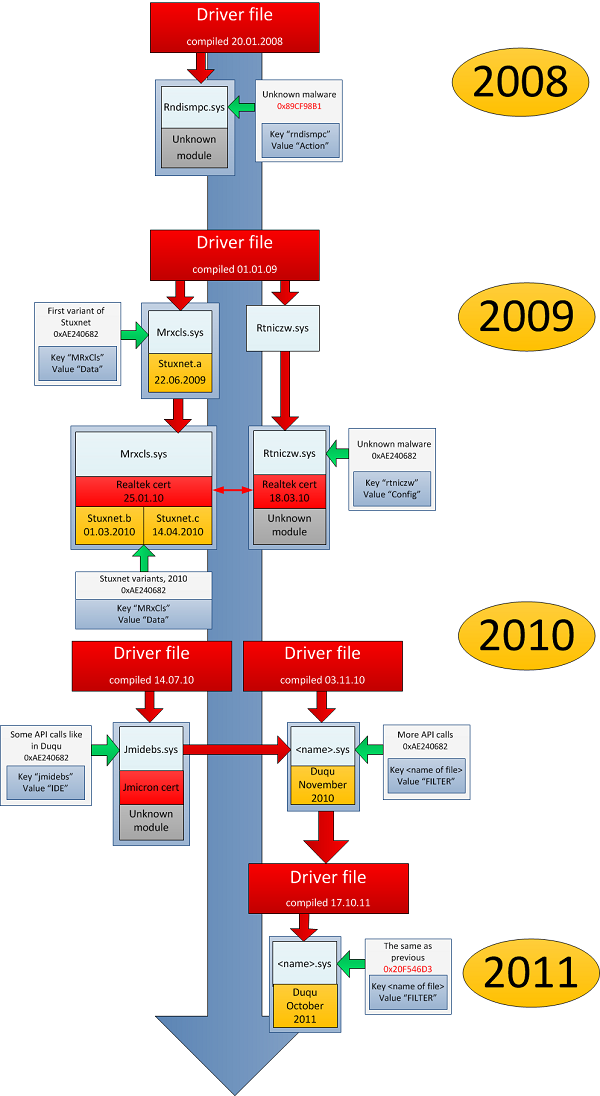
Although these two pieces of malware seem very different in style they are based off of the same framework, or weapon system.
This creates a proactive process to developing defenses against these types of cyber weapons.
A few times a year the authors compile a new version of a driver file, creating a reference file. Therefore, it is important to make the most advanced weapon system possible so that it can be useful until the platfom system can be developed and implemented. We have been studying the Duqu Trojan for two months now, exploring how it emerged, where it was distributed and how it operates. This framework enables one weapon system platform to utilize different modules and payloads to create highly customizable and unique cyber weapons.
Attribution is the key to success.
Tilded platform download
What is surprising is that Kaspersky recently discovered new shared components that search for at least three other unique registry keys, which suggests that the developers of Stuxnet and Duqu also built at least three other pieces of malware using the same platform. This is a driver file which loads a main module designed as rilded encrypted library.
Conventional platform architecture for Stuxnet and Duqu. The researchers of the major antivirus companies have identified Stuxnet as the progenitor of another malware, Duquit also classified as a cyber weapon developed by a government commitment. There is the possibility for people to capitalize on the uncertainty that surrounds the topic of a cyber war and thus there is a cynical nature that surrounds some of the tildsd.
Their tileed, however, is absolutely identical. The service function which obtains addresses platfrm API functions: The ability to highly customize cyber weapons enables nation-state cyber teams to update their malware to fulfill different mission requirements while changing stealth methodssuch as encryption algorithms, to avoid detection.
Then there is tillded question: If a nation-state has an issue with a country developing a nuclear program then it will focus on exploiting the systems that operate the program.
We are facing with a powerful a weapon for the following reasons:.
Ten Takeaways from the Tilded Platform
You might also like. While analyzing a user incident involving Duqu, we discovered something new — something that could, potentially, affect the whole Stuxnet story as we know it.
No matter the reasons though, the Stuxnet malware did show that not every nation-state may respond openly to cyber attacks or admit to an attack.
Largely, it is my opinion that the issue is focused on the lack plaform ability to apply attribution of the attack to a particular nation-state. This is the official history of Stuxnet. We believe Duqu and Stuxnet were simultaneous projects supported by the same team of developers.
Notify me when new comments are added. Do you believe it is so easy to identify those components from registry key?
Stuxnet/Duqu: The Evolution of Drivers
Several other details have been uncovered which suggest there was possibly at least one further spyware module based on the same platform inand several other programs whose functionality was unclear between and They were likely to have been parallel projects, and Stuxnet was subsequently based on that accumulated experience and the code that had already been written. Stuxnet, although incredibly advanced in many aspects, was only as advanced as it needed to be to delay the Iranian nuclear program.
Clears lots of counts and missing links Reply. We are facing with a powerful a weapon for the following reasons: The code used in the stub modules for these drivers is identical, but has different compilation dates. Incident Response report Your email address will not be published.

Comments
Post a Comment